Recently I got the opportunity for migrating one of the Azure
customer from his existing IPSEC VPN to Express Route. After doing some research
and going through multiple scattered documentation, I was able to do the
migration successfully. The whole process will normally take around 90 to 120
minutes. I decided to make this post to consolidate the entire process together
for future migration.
Assuming that the Express Route is already provisioned by your
provider, the procedure goes as follows:
1. During the initial IPSEC VPN configuration, gateway subnet
was created. For IPSEC VPN, the length of the subnet is /29 but for Express Route the length has to be /28. Unfortunately you can’t
change this subnet if the IPSEC VPN is still in use.
2. In order to change the gateway subnet, you need to first delete the IPSEC VPN under VIRTUAL NETWORK GATEWAY --> CONNECTIONS
3. Delete the VIRTUAL NETWORK GATEWAY. This step can sometimes take upto 30 to 40 minutes.
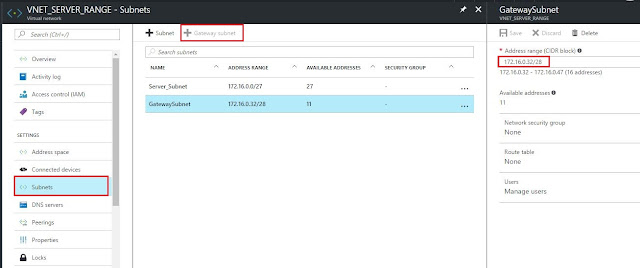
4. Delete the gateway subnet under VIRTUAL NETWORK --> SUBNETS --> GATEWAYSUBNETS and create it with /28 as the mask.
5. Create the VIRTUAL GATEWAY again but this time select the gateway type as EXPRESS ROUTE. Select the appropriate VIRTUAL NETWORK and RESOURCE GROUP. Note that you have to select PUBLIC IP ADDRESS as well but it won't be used for Express Route configuration. This step will again take upto 30 to 40 minutes.
6. Last step will be to link your EXPRESS ROUTE connection with the VIRTUAL NETWORK. For that, you need to go to EXPRESS ROUTE --> CONNECTIONS --> ADD. Select the appropriate VIRTUAL NETWORK GATEWAY (created above) and EXPRESS ROUTE CIRCUIT.
7. Once the EXPRESS ROUTE is linked to VNET successfully, your provider should start receiving the VNET subnet on the BGP session.






![SD-WAN topology diagram indicating the relationship between a headquarters and branch site, incorporating MPLS, IP-sec, VoIP, 4G LTE, firewall, SaaS, and the public internet.]](https://www.windstreambusiness.com/media/942290/sd-wan-diagram.gif)